Amazon Managed Grafana - Entra ID SAML Group Attribute

Introduction
Recently I was tasked with investigating the process of integrating Entra ID with Amazon Managed Grafana through SAML. While this wasn't a challenging task, I did run into a few issues that I thought would be worth documenting for others.
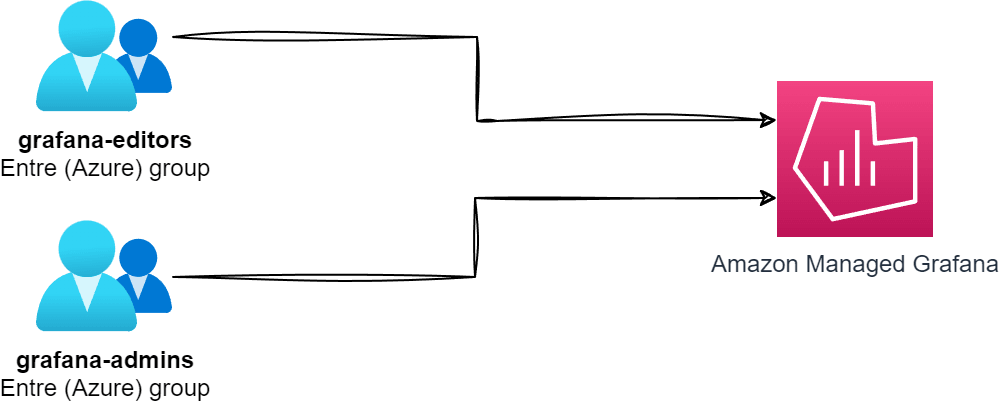
Currently, the documentation on both the Entra ID and Amazon Managed Grafana sides lacks any practical examples of how to configure the SAML integration. More specifically, the number one use case I expect to see is configuring group-based access control to Grafana. This is a common use case, and I was surprised that there was no documentation on how to do this.
The existing guides that exist for configuring Amazon Managed Grafana with SAML are pretty good - so I won't be covering the entire process here. For reference:
- Tutorial: Microsoft Entra single sign-on (SSO) integration with Amazon Managed Grafana
- Amazon Managed Grafana supports direct SAML integration with identity providers
Once you have followed one of the guides above, you will probably notice that I mean by the lack of documentation/instructions on configuring an attribute for groups - and you are good to move on to the next steps, where I will cover how to do it!
Create a group Attribute in Entra ID
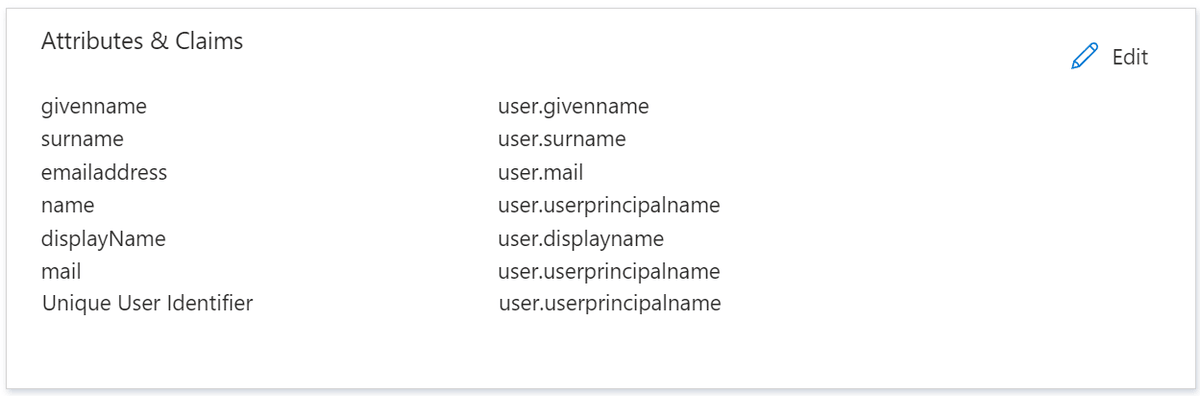
Find the Entra ID Enterprise Application you created when configuring the SAML integration with Amazon Managed Grafana. In the Enterprise Application, click Single sign-on to see an Attributes & Claims section.
By default, when creating the Enterprise Application in Entra ID, the following attributes are created:
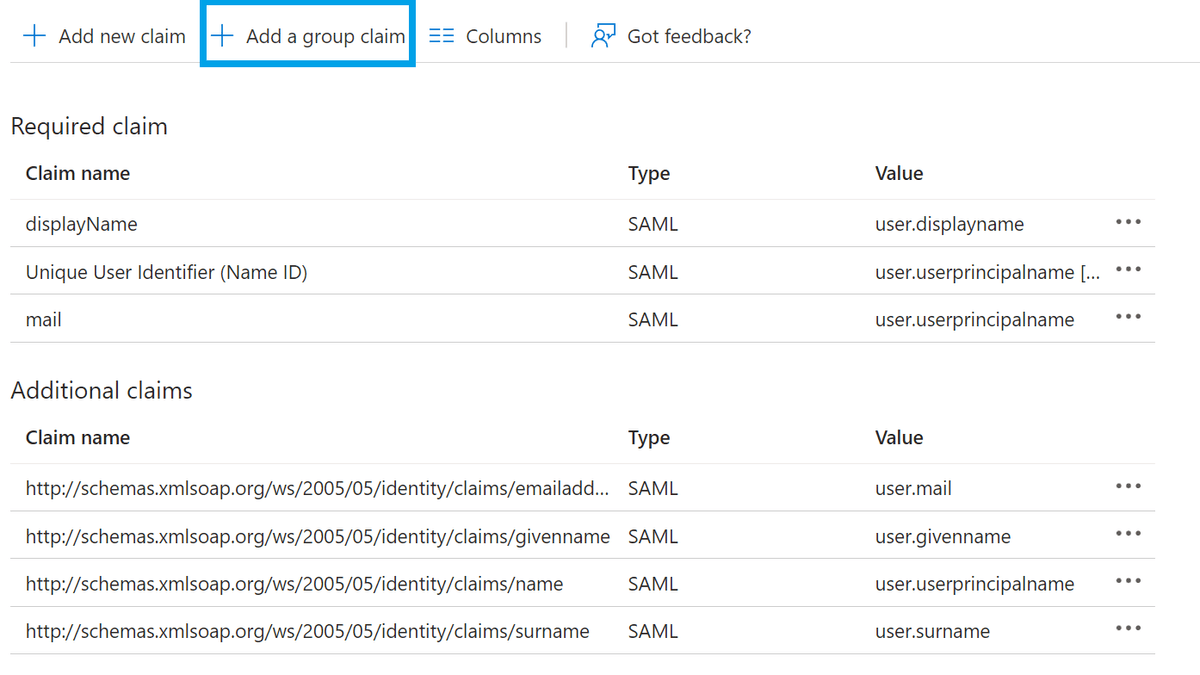
We will add a new attribute called groups, which will pass a list of Entra ID groups to Amazon Managed Grafana. Click Edit and then Add a group claim:
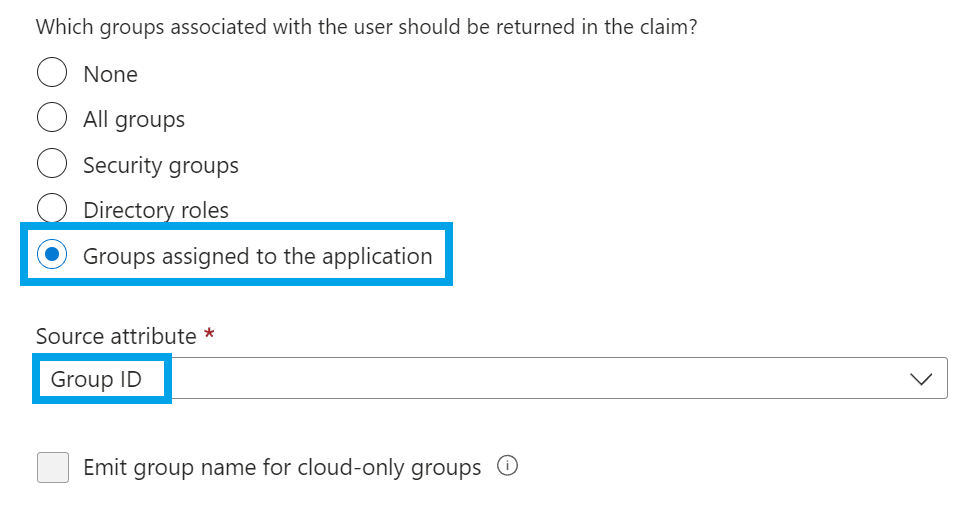
When asked for which groups associated with the user should be returned, select Groups assigned to the application
Also, confirm that the source attribute has Group ID selected.
Under Advanced options, make sure to select Customize the name of the group claim and enter groups as the name.
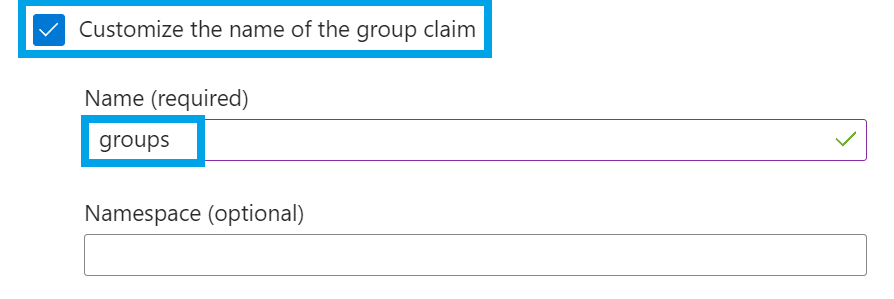
Assign Groups to Entra ID Enterprise Application
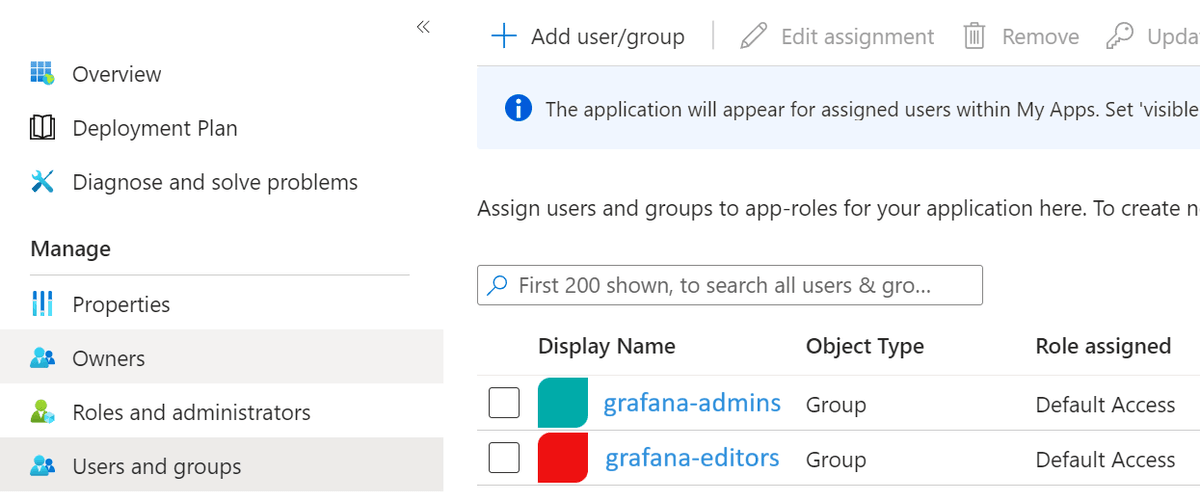
Now that we have created the groups attribute, we must assign some groups to the Enterprise Application. This is done by clicking Users and groups and then Add user/group:
Select the groups that you want to assign - in my case, I am assigning the grafana-admin and grafana-editor groups - take note of the Object ID for each group, as we will need this later.
Modify the Amazon Managed Grafana SAML Configuration
Finally, we need to modify the SAML configuration in Amazon Managed Grafana to tell it to look for the groups attribute we created in Entra ID.
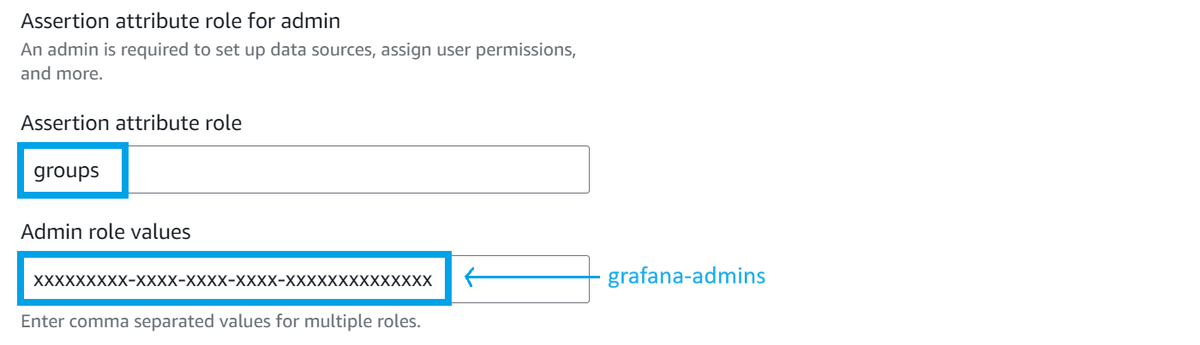
For the Assertion attribute role, change the value to groups to match the attribute's name we created in Entra ID.
Also, provide the Entra ID Object ID for the group(s) you want to assign Admin permissions to.
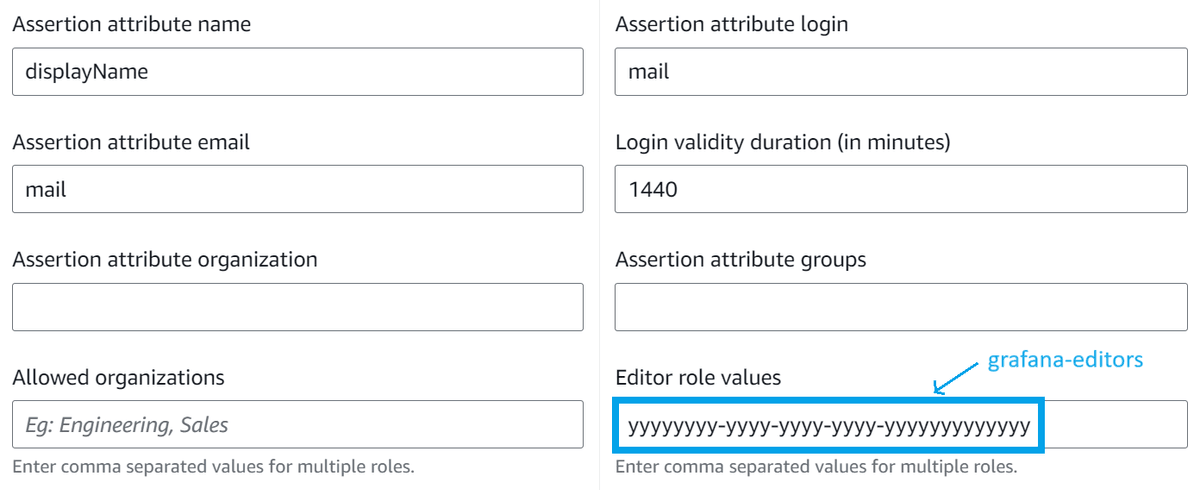
Open Additional settings - optional and specify the Entra ID Object ID for the group(s) to which you want to assign Editor permissions in the Editor role values field.
Conclusion
That's it! You should now be able to log in to Amazon Managed Grafana using Entra ID and automatically assign your users to the correct group based on their Entra ID group membership.
Hopefully, this guide will help others looking to do the same thing. If you have any questions or comments, please feel free to reach out to me on Twitter or LinkedIn.